In today’s world, privacy and security have become paramount. As more people opt to use Virtual Private Networks (VPNs) to secure their internet connections, the use of email services has also seen a shift. One such popular email service is Spark Email, a favorite for many users due to its …
Sour Sharks VPN Ara Crome
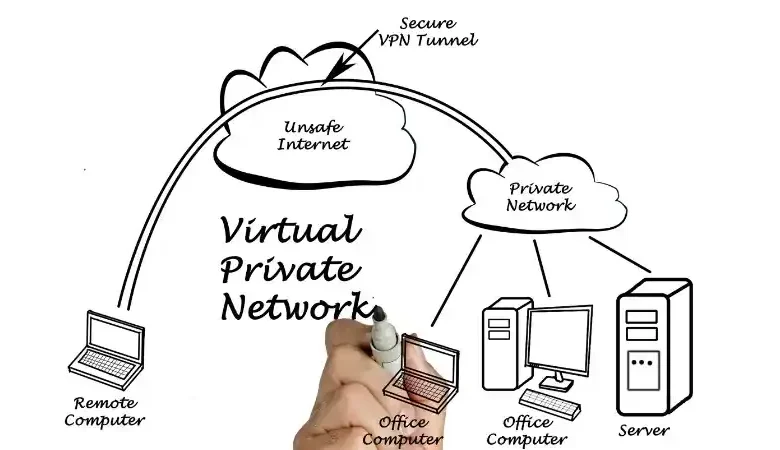
With the increasing need for online security, VPNs (Virtual Private Networks) have become essential tools for protecting privacy and accessing restricted content. One such powerful VPN solution is Sour Sharks VPN Ara Crome, which stands out due to its robust encryption, speed optimization, and ease of use. This article explores …
Running VPN While Playing GSPro
GSPro has become one of the most advanced golf simulation software options available, providing an immersive experience for players worldwide. As online connectivity plays a significant role in delivering real-time gameplay and updates, some users opt for running VPN while playing GSPro to enhance their gaming experience. However, using a …
Ensuring Torrenting Security with qBittorrent VPN Binding
In the digital age, privacy has become a crucial concern for internet users, particularly when engaging in activities such as torrenting. As a popular and widely-used open-source torrent client, qBittorrent offers numerous features that appeal to users worldwide. However, like all torrenting activities, privacy risks can arise if proper safeguards …
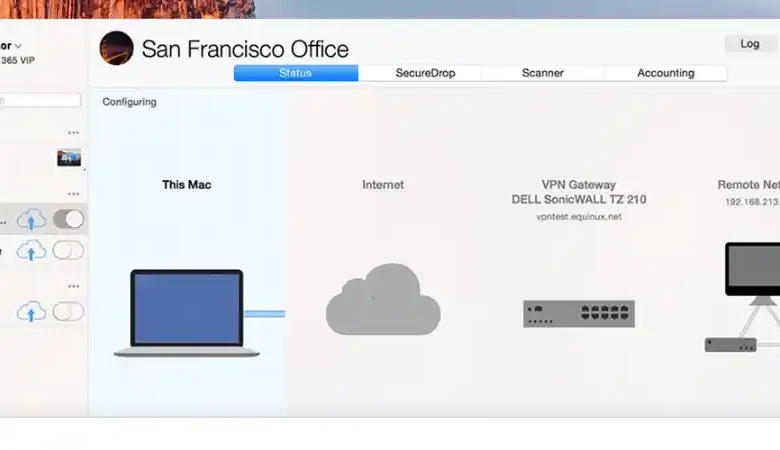
Traffic for Mobile VPN with SSL on macOS (12.10.4)
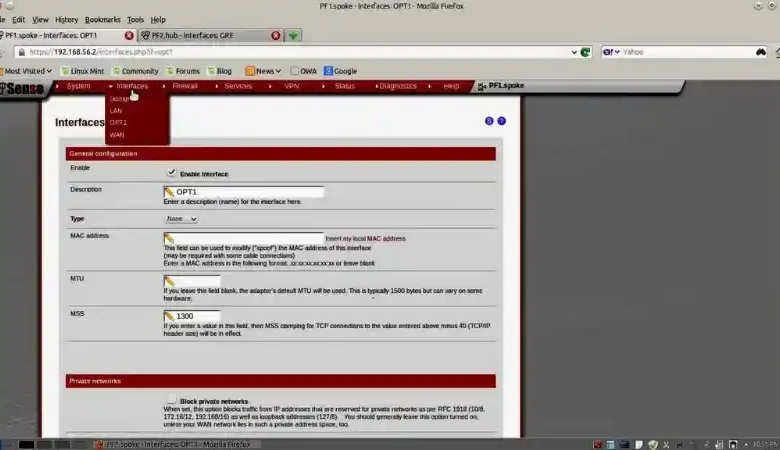
In today’s digital landscape, secure communication is more important than ever. Virtual Private Networks (VPNs) offer a robust solution for ensuring privacy and data integrity when accessing the internet, particularly for mobile users and remote workforces. However, network issues like packet fragmentation can impede the smooth operation of VPN connections. …
Mobile VPN with SSL 12.10.4 for macOS Mac
In today’s digital world, security and privacy are top concerns for individuals and businesses. Mobile VPN with SSL 12.10.4 for macOS Mac is a robust solution designed to provide secure remote access to networks, ensuring data confidentiality and integrity. This article explores the features, installation, setup, and benefits of Mobile …