In today’s digital landscape, secure communication is more important than ever. Virtual Private Networks (VPNs) offer a robust solution for ensuring privacy and data integrity when accessing the internet, particularly for mobile users and remote workforces. However, network issues like packet fragmentation can impede the smooth operation of VPN connections. This is where MSS clamping comes into play, particularly when configuring VPN traffic through pfSense, a highly flexible open-source firewall and router platform.
This guide will walk you through how to pfSense enable MSS clamping on VPN traffic for a smooth and secure mobile VPN setup using SSL on macOS 12.10.4. By the end of this article, you’ll be able to configure MSS clamping to enhance the stability and speed of your VPN connection.
What is MSS Clamping
Maximum Segment Size (MSS) refers to the largest amount of data a device is willing to receive in a single TCP packet. When MSS clamping is enabled, pfSense will modify the MSS value in the TCP headers of packets that pass through it. This can help prevent packet fragmentation, which often occurs when a packet exceeds the maximum transmission unit (MTU) of the network. Packet fragmentation leads to performance degradation, latency, and packet loss, negatively impacting the quality of the VPN connection.
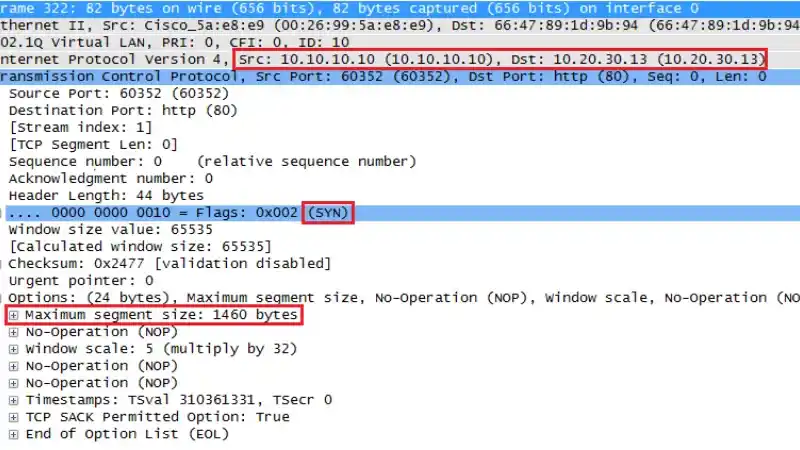
MSS clamping adjusts the size of the packets before they are transmitted over the network to ensure that they do not exceed the MTU, preventing fragmentation and thus improving performance. Enabling MSS clamping is particularly useful for VPN traffic because it ensures that the VPN packets can pass through routers and firewalls without any issues.
Why Enable MSS Clamping on VPN Traffic
Enabling MSS clamping on VPN traffic helps prevent fragmentation, ensuring that packets are appropriately sized to fit within the available MTU. This results in smoother and more efficient VPN traffic, minimizing the possibility of dropped packets or poor performance.
MSS clamping improves overall VPN performance by ensuring that the network traffic is processed optimally, reducing latency and congestion that could otherwise hinder connection quality. Furthermore, it helps address potential issues related to packet loss, which is particularly critical for mobile users on macOS 12.10.4, who may encounter connectivity issues due to improper packet handling.
Enabling this setting ensures that SSL VPN traffic is properly optimized, allowing it to pass through the network without interference, ensuring smooth and uninterrupted mobile VPN usage.
How to Enable MSS Clamping on VPN Traffic in pfSense for SSL VPN on macOS 12.10.4
To begin, log into your pfSense router by navigating to the pfSense device’s IP address in your web browser. Once logged in, you can access the dashboard where you will configure the SSL VPN settings.
Make sure that SSL VPN (OpenVPN or IPsec) is configured correctly on pfSense before enabling MSS clamping. If you are using OpenVPN, go to the VPN > OpenVPN section of pfSense, ensuring the necessary SSL VPN settings are configured. If you are using IPsec, navigate to the VPN > IPsec section and configure the appropriate settings.
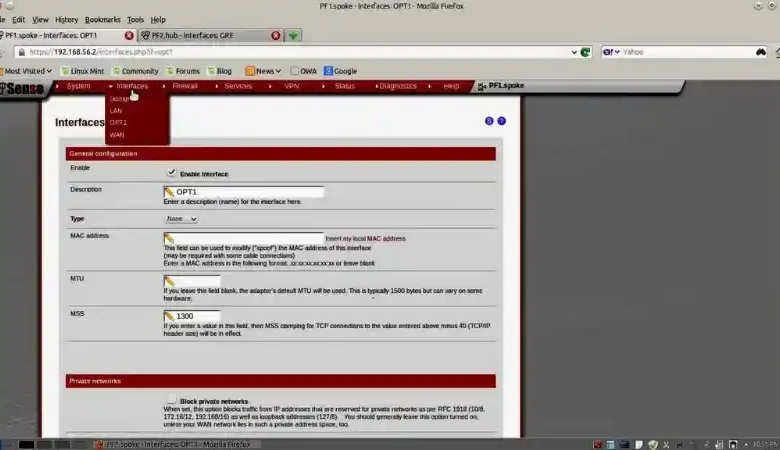
Once the VPN server is set up and functional, you can modify the MSS clamping settings within the Firewall Rules configuration. Go to Firewall > Rules, select the interface where VPN traffic is flowing, usually the WAN interface, and either edit an existing rule or create a new one.
In the rule configuration, look for the Advanced Options section and locate the MSS Clamping setting. Set the MSS value to a preferred size, usually around 1400, though this can be adjusted depending on the network’s requirements. Once the changes are made, click Save and apply the changes for the settings to take effect.
After configuring the MSS clamping on pfSense, test the VPN connection from a macOS 12.10.4 device. Launch the SSL VPN client, connect to the VPN, and observe the performance. If the connection is stable and there are no packet loss or performance issues, your configuration has been successful.
Additional Tips for Improving VPN Performance
If you continue to face issues, consider adjusting the MTU size in your VPN client settings or on the pfSense interface. This could further help reduce fragmentation and improve the connection speed. Also, ensure that your pfSense installation is up-to-date, as newer versions may contain important performance improvements or bug fixes. Regularly monitoring the VPN connection and fine-tuning the settings will help maintain optimal performance.

If issues persist, try switching between different VPN protocols such as OpenVPN or IPsec, depending on which one performs better in your specific network environment.
Common Issues and Troubleshooting
If you experience frequent disconnections despite enabling MSS clamping, double-check the firewall rules to ensure there are no conflicting settings that could be interfering with the connection. In cases of slow VPN speeds, it may be helpful to adjust the MSS value further or experiment with lowering it slightly to improve throughput. For any connectivity issues on macOS 12.10.4, verify that the SSL VPN configuration is correct and that the necessary certificates are properly set up.
Enhancing Your VPN Experience with MSS Clamping
Enabling MSS clamping on VPN traffic in pfSense is an essential network optimization technique that can dramatically improve the performance of SSL VPN connections. It ensures that packets are properly sized, reducing the risk of fragmentation and enhancing the overall stability of the connection. This is especially useful for mobile users on macOS 12.10.4, where network issues like packet fragmentation are more prevalent.
By following this guide, you will be able to configure MSS clamping on your pfSense router, optimizing your VPN connection for a better and more secure browsing experience. Keep monitoring your VPN performance and adjust the settings accordingly to ensure that your network remains efficient and stable.